
Demystifying Cybersecurity: An Introduction for Business Leaders
By Ash Ryan Arnwine on 1/6/2025
- cybersecurity
- vendor management
- professional services
Let’s face it: for most people in business, cybersecurity feels like an overwhelming maze of technical jargon and endless threats. But given that most things start and end online, understanding cybersecurity isn’t just for IT professionals anymore—it’s a business imperative that touches every aspect of modern operations.
If the average developer struggles to keep up with the latest security trends, how can business leaders be expected to navigate this complex landscape? The good news is that you don’t need to be a cybersecurity expert to understand the basics and make informed decisions about your organization’s security posture.
What is Cybersecurity, Really?
At its core, cybersecurity is about protecting three fundamental aspects of our digital assets: confidentiality, integrity, and availability (or “CIA”).
Think of it like securing your home:
- You want to keep unwanted visitors out (confidentiality),
- Ensure nothing inside gets tampered with (integrity), AND…
- Maintain access for authorized people (availability) .
Easier said than done when threats and defences are changing constantly. What started as simple username/password combinations has transformed into sophisticated, layered defense systems. You might remember a time when two-factor authentication felt cutting-edge (your periodic reminder to ask yourself “Is SMS for 2FA/MFA secure?”); now we need to consider zero-trust architectures and AI-powered threat detection.
Modern cybersecurity has become a comprehensive discipline, encompassing everything from protecting sensitive customer data to maintaining business operations during ransomware attacks. Through each advance in technology and shift in approach, one thing remains constant: the need to stay ahead of increasingly sophisticated threats.
Why Should You Care About Cybersecurity?
A sobering reality: according to IBM’s Cost of a Data Breach Report 2024, the average cost of a data breach reached $4.88 million last year. But beyond the financial impact, cybersecurity breaches can shatter customer trust and damage reputations that took years to build.
Consider the 2023 breach at Latitude Financial Services, where cybercriminals accessed over 200,000 customer records containing drivers’ licenses, passports, and other sensitive data. The immediate costs were reported at AU$76 million in incident response alone, but the longer-term impact on client trust and new business acquisition was far more significant. This isn’t just about protecting data—it’s about protecting your business’s future.
On top of breach-related risks, regulatory requirements like GDPR and CCPA have made cybersecurity a legal imperative. Non-compliance can result in hefty fines and legal complications that no business wants to face.
So we get it: cybersecurity is a “must-have” for any business. The question is, how do you navigate this complex landscape and ensure your organization is protected?
Key Areas of Cybersecurity You Need to Know
Understanding cybersecurity becomes much clearer when we break it down into its core components. Even if the technical landscape constantly evolves, certain fundamental areas remain critical for any comprehensive security program.
A solid go-to standard is the NIST Cybersecurity Framework (CSF), which provides a comprehensive approach that any organization can adapt to their needs.
NIST CSF 2.0 prescribes 6 key functions every business needs to understand: Govern, Identify, Protect, Detect, Respond, and Recover.
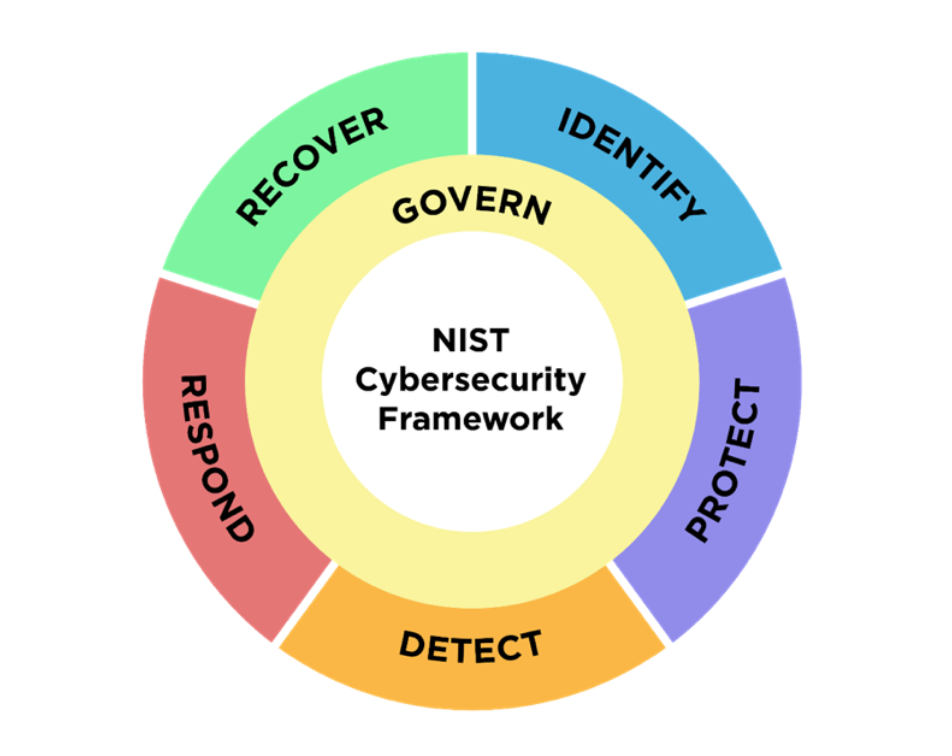
Let’s take a quick look at each.
Govern
This is where it all starts. Governance isn’t just about having policies; it’s about establishing your organization’s cybersecurity North Star. This includes setting your strategy, defining roles and responsibilities, and ensuring your cybersecurity efforts align with your business objectives. Think of it as the foundation that supports everything else you do in cybersecurity.
Identify
This is all about understanding what you’re protecting. Organizations often struggle here because they can’t protect what they don’t know they have. This involves maintaining inventories of your hardware, software, and data, understanding your business environment and critical dependencies, assessing risks across your digital landscape, and identifying opportunities for improvement in your security processes.
Protect
Here you are implementing safeguards to ensure your critical infrastructure services. This is the stuff you’ve encountered day-to-day. It includes things like identity and access management (IAM), security awareness training (because your people are your first line of defense), data security (protecting information at rest, in transit, and in use), platform security (securing both physical and virtual environments), and technology infrastructure resilience. As a business leader, you might not need to know the technical details of each of these areas, but you should understand the importance of each and how they contribute to your overall security posture.
Detect
Detection capabilities are crucial, but this isn’t just about having security tools; it’s about implementing continuous monitoring across your networks and systems, analyzing potential security events, maintaining awareness of emerging threats and vulnerabilities, and understanding normal versus abnormal behavior in your environment.
Respond
When incidents occur (and they will), having a well-planned response is critical. This includes incident management procedures, clear communication protocols, analysis and mitigation strategies, and methods for learning from incidents to prevent future occurrences.
Recover
The final piece of the puzzle is recovery – getting back to normal operations after an incident. Key aspects include executing recovery plans, managing communications during recovery, implementing improvements based on lessons learned, and verifying the integrity of restored systems and data.
Success in cybersecurity isn’t about perfecting any single area—it’s about maintaining a balanced approach across all these domains while staying agile enough to adapt to emerging threats. This complexity is precisely why many businesses find themselves seeking external expertise.
Why Businesses Turn to External Cybersecurity Partners
Most organizations struggle to maintain comprehensive cybersecurity programs internally. The landscape changes too quickly, threats evolve too rapidly, and the required expertise is too specialized.
This is where external cybersecurity partners become invaluable. They bring:
- Specialized expertise across multiple security domains
- Up-to-date knowledge of emerging threats
- Scalable solutions that grow with your business
- 24/7 monitoring and incident response capabilities
- Compliance expertise across different regulatory frameworks
These capabilities, when kept up-to-date and battle-tested, often make the difference between a robust security posture and a vulnerable one. Recognizing the need for partners is hopefully the easy part—finding the right ones is where it gets tricky.
Finding the Right Cybersecurity Partner
Selecting a cybersecurity partner is a critical decision that requires careful evaluation of their capabilities, experience, and alignment with your business needs. This is where sc0red comes in.
Our platform helps you:
- Access detailed, unbiased assessments of cybersecurity providers
- Compare capabilities across multiple vendors
- Verify technical expertise and certifications
- Make data-driven decisions about your security partnerships
Through our comprehensive assessment framework, we’ve simplified the complex process of vendor evaluation, allowing you to focus on what matters most: building a secure and resilient business infrastructure.
Moving Forward
Cybersecurity is only becoming more critical as attack vectors evolve (“adversarial machine learning”, anyone?). The key is not to view it as a burden but as a business enabler that provides the foundation for digital innovation and growth. Firms that execute on sound cybersecurity strategies will win the day.
Start by assessing your current security posture and identifying gaps. Consider where external expertise might strengthen your defenses. Remember, cybersecurity is not a one-time project but an ongoing journey of adaptation and improvement.
Ready to find the right cybersecurity partner for your business? Visit sc0red to explore verified cybersecurity providers and make an informed choice based on comprehensive, data-driven assessments.
Find the right cybersecurity partner with sc0red
Make confident decisions with unbiased assessments of companies across the market.